This article is more than 1 year old
Targeted, custom ransomware menace rears its ugly head
No spraying and praying here, just precise, exorbitant attacks
Attackers are manually deploying ransomware directly into target networks to maximise the damage and potential payout.
Unlike "spray-and-pray" attacks such as WannaCrypt, which hit victims at random, targeted attacks that manually execute the ransomware enable criminals to ensure they have locked mission-critical files that companies will be most likely to pay exorbitant fees to retrieve. Manual deployments can also evade most traditional signature-based security measures, making it much harder to identify and stop before it's too late.
Matt Hillman, a principal security researcher at MWR InfoSecurity, said the custom ransomware associated with these attacks is typically getting distributed through phishing emails rather than software exploits. The attacks are targeted against banking and infrastructure firms worldwide.
"This ransomware is targeted at big organisations because the amount they are prepared to pay is greater," Hillman explained. "Hackers are timing their attack to add pressure," for example by launching assaults just before sales quarters close or a major announcement or industry event.
The attacks are more geared at making money than causing disruption, unlike the recent NotPetya outbreak.
Sean Sullivan, a security advisor at F-Secure, said that its labs haven't seen any "bespoke" ransomware as such but it has seen some file-encrypting malware variants "aimed very selectively". F-Secure uncovered chat sessions in which a ransomware support agent claimed they were hired by a corporation for targeted operations (see page 15 of this PDF). "There was some analysis/metadata that we later used to find another variant which seemed to support that claim," Sullivan told El Reg, adding that the follow-up attack targeted IP lawyers and was seemingly aimed as disrupting their business operations.
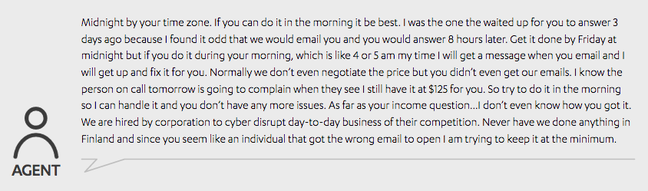
Ransomware support agent casually chats about targeted malware work to supposed victim [source: F-Secure white paper]
Raj Samani, chief scientist at McAfee, added that targeted ransomware might be used for obscuring attacks actually aimed at data exfiltration. This would give better "better plausible deniability" than traditional wiper-style attacks, he added. Wiper attacks in the past have included the Shamoon assaults on oil company Saudi Aramco and other targets.
Researchers approached by El Reg cited one already recognised example of manually deployed ransomware. Crooks behind the SamSam ransomware typically charge very high ransoms because of the amount of effort invested in their operations.
Defending against SamSam is more akin to a targeted attack than typical opportunistic ransomware, an article by security tools firm AlienVault explains. SamSam attackers have broken into corporate networks using JBoss exploits or similar before deploying web shells and running batch scripts to deploy the ransomware on machines.
"The attacks seem to peak in waves as campaigns distributing SamSam are executed," AlienVault's Chris Doman reports. "A notable recent example was a large hospital in [upstate] New York that was hit with SamSam in April. The hospital declined to pay the attackers the $44,000 ransom demanded. It took a month for the hospital's IT systems to be fully restored."
Last month SamSam variants appeared that demanded 12 Bitcoins ($32,800) to receive data on all infected machines or 1.7 Bitcoins ($4,600) for a single machine. "The ransom the victims must pay to recover their files is hardcoded in the malware," AlienVault added.
Extortionate demands for regular spray-and-pray ransomware vary widely but at the lower end come out at $300 per infection, so targeted ransomware demands can be at least 10 times higher by that estimate.
Targeted ransomware will only increase, according to Bart Parys, a threat intelligence expert at PwC.
MWR's Hillman advised organisations to review their security policies in order to better defend against custom malware, adopting an approach he described as "containment by design". This would involve giving users and software the least possible privileges (the security perils of running too much stuff as admin was, of course, illustrated the the recent NotPetya outbreak); using security packages capable of blocking malicious behaviour; and network segmentation. Businesses should also develop a recovery plan before testing it to make sure they have an effective disaster recovery strategy in place, he added. ®
