This article is more than 1 year old
Hackers able to turbo-charge DJI drones way beyond what's legal
Well, if you are going to leave debug code in production apps
Drone hackers in the UK are busy at work exploiting the application security shortcomings of a major manufacturer to circumvent restrictions, including flight elevation limits. DJI says it has pushed out a firmware update to nip the problem in the bud, but one expert The Register spoke to maintains that hacking is still possible.
The potential for drone hacking can be traced back to a mistake made by DJI in leaving development debug code in its Assistant 2 application. Changes could be made by commenting out one line in a file and setting the debug flag from false to true. The shortcoming exposed a full range of parameters that enabled hackers to turn off safeguards.
"It's looks like #DJI's #Spark was jailbroken due to poor app security? Leaving dev code & passwords in the app was probably not a good idea," UAVHive, a UK-based drone enthusiast community, said in a Twitter update.
Other DJI products – including the Phantom and Inspire 2 – have had the same jailbreak proven.
DJI has been warned repeatedly since at least April, if not before, by Kevin Finisterre, a drone security expert, among others. Despite this, critics say DJI failed to act.
Concerns centre on the application security risks posed by the presence of DJI debug code in publicly released applications, something that creates a backdoor for hackers to meddle with the technology.
Recently numerous underground groups of drone users have sprung up and are collaborating on removing restrictions from their drones and even change performance parameters. For example, a Facebook group for drone enthusiasts included hackers in its ranks. A Slack group is even more active and seems to be where a lot of the actual effort is taking place, we're told.
"The main focus of efforts is removing height restrictions with ongoing efforts to remove no-fly zones, there's even secret groups of drone pilots now having height competitions to see who can push their drone's performance the furthest," a source told El Reg. "A lot of this extreme behaviour by DJI owners is a direct backlash at DJI for adding a range of restrictions including having to connect to their servers via the internet. Recently, for example, DJI's infrastructure was down and users complained they were grounded as a result. The no-fly zone database has many false positives."
Coding is steadily under way to simplify the removal of restrictions such as NFZs (no-fly zones) and turbo-charge performance of DJI drones.
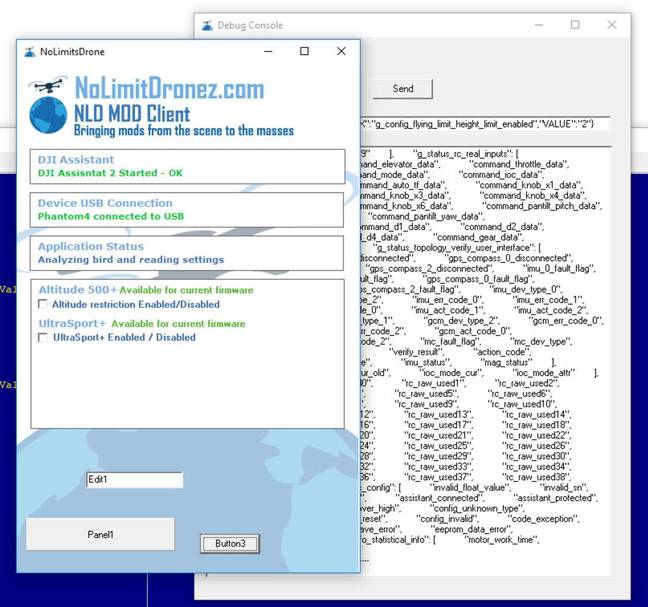
A "no limit" drone app
"Users have been able to increase radio range, which breaches EU laws," one expert, who did not wish to be named, told El Reg. "This allows the drones to fly further (keeping in mind the UK legal limit is 500m distance from the pilot) but owners are flying miles."
UK laws for recreational flights are summarised here. Height limits are explained here.
Height limits have been removed, allowing users to circumvent safety restrictions that ought to apply to their kit. Thanks to various hacks, users have been posting online photos/video at heights well above the 120m limit.
The process is not complicated and has even gone mainstream, as illustrated by a YouTube video on how to modify DJI drone flight parameters to remove altitude restrictions (below).
El Reg ran the app security aspects of this by security consultant Ken Munro, who told us it looks like DJI failed to follow industry best practice.
"It's a bit silly to leave debug code in production apps," Munro said. "Particularly so because DJI were informed of this and could easily have pushed a new app version with the offending code removed. Note they released Assistant 2 v1.1.2 on June 16. I'm not clear if it's this version that has the problem, or if they've just fixed it."
DJI told The Register that it had issued software updates in response to reports of unauthorised firmware modifications.
A recent firmware update for Phantom 4 Pro, Phantom 4 Advanced, Phantom 3 Standard, Phantom 3 SE, Mavic Pro, Spark, and Inspire 2, among others, fixes reported issues and ensures DJI's products continue to provide information and features supporting safe flight. DJI will continue to investigate additional reports of unauthorised firmware modifications and issue software updates to address them without further announcement.
Victor Wang, DJI Technology security director, reiterated that DJI's geofencing features (which provide "no-fly zone" data) are designed specifically to provide information to DJI customers about airspace where drone flight raises serious safety or security concerns. He also said that DJI continually monitors modifications to its drones that might make their operations "non-compliant with best safety practices".
"Modifying the firmware of a DJI drone is not recommended, as it can cause unstable flight behaviour that could make operating the drone unsafe. DJI is not responsible for the performance of a modified drone and we strongly condemn any user who attempts to modify their drone for illegal or unsafe use."
Users authorised to fly in restricted areas can either unlock these zones using DJI's GEO system or by submitting a request to the company by email. DJI added that it offers a software development kit (SDK) for creating customised software using its platforms.
Finisterre, whose previous exploits include extracting DJI's NFZ database from an application, was unimpressed with the drone maker's latest statement. "The bugs that I disclosed that were circulating in the underground have NOT been fixed for what it is worth," he told The Reg.
The drone security expert went on to criticise DJI's procedures for allowing authorised parties to remove restrictions, saying that they have proved ineffective. Unable to successfully apply to remove restrictions, a growing body of enthusiasts have resorted to hacking the software on their UAVs, it seems.
Finisterre added: "You'll find plenty of users that claim they are unable to unlock... I live in an NFZ, for example, and have permission, the app built-in functionality never ever worked for me, either the phone call, or credit card unlock." ®
