This article is more than 1 year old
Another IoT botnet has been found feasting on vulnerable IP cameras
Children, please welcome Persirai to the class
Researchers have discovered yet another IoT botnet.
Persirai targets more than a thousand different internet protocol camera models. Researchers at Trend Micro warn that 120,000 web-connected cameras are vulnerable to the malware.
Consumers would, in most cases, be unaware that their devices are even exposed to the internet much less at risk of compromise. Hackers are using a known but seldom patched vulnerability to hack the cameras.
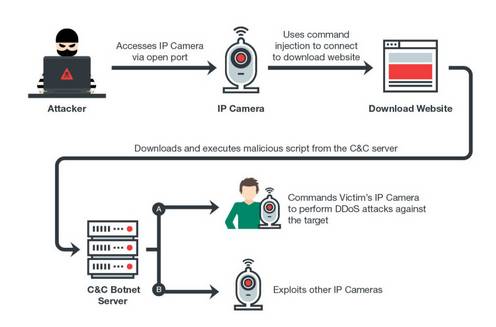
Persirai malware infection flow [Source: Trend Micro bog post]
The development of Persirai comes just weeks after the arrival of Hajime – the "vigilante" IoT worm that blocks rival botnets – and months after the infamous Mirai IoT botnet. Mirai was used to attack a key internet domain resolution hub last October, leaving scores of high-profile websites unreachable to millions.
Unlike its relatives, Persirai sticks to IP cameras rather than also going after internet-connected digital video recorders, routers, and other vulnerable IoT devices. The targeting might be down, at least in part, to how easy IP cameras are to hack.
"IP cameras typically use Universal Plug and Play (UPnP)... making them highly visible targets for IoT malware," Trend Micro researchers Tim Yeh, Dove Chiu and Kenney Lu note. ®
