This article is more than 1 year old
Insecure Hadoop installs next in 'net scum crosshairs
Because MongoDB, Elasticsearch ransomware attacks are sooo last week
Rinse-and-repeat ransomware attacks on data services left unsecured by dozy sysadmins are now hitting Hadoop instances.
Fidelis Cybersecurity reckons it's started observing the attacks, which seek out default installations of the big data darling, copy and then wipe Hadoop instances and then demand a ransom for return of victims' data.
The company's post notes that the victims are often using platform-as-a-service hosts, meaning they can't operate with only local connections. This mandatory 'net access makes it more important that the install be secured.
The post estimates the current exposure at between 8,000 and 10,000 instances worldwide.
Backing up Fidelis' assessment is data from the SANS Internet Storm Center, which early in January spotted a spike in scans to port 50070 (the default for Hadoop's namenode service, looking for the Hadoop Distributed File System.
Qihoo's 360 Netlab saw a similar spike, claiming that almost all the scans came from just two IP addresses in China. As the post notes, however: “it's important not to jump to conclusions about the attacker's location simply by looking at an IP address. Attackers use infrastructure all over the world to hide their identities”.
In one of the attacks Fidelis observed, the attacker didn't even give the user the chance to get a ransom: they deleted all directories, and left behind their own directory, /NODATA4U_SECUREYOURSHIT [At least they didn't spell it “you're” - Ed).
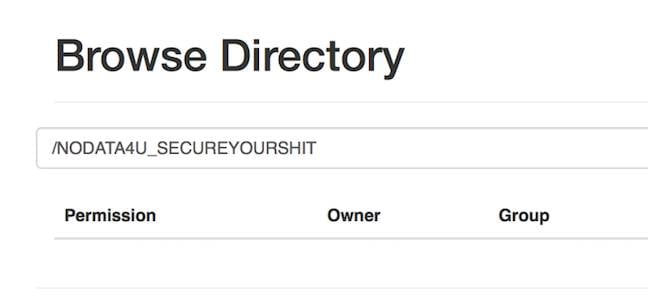
Victim's screen, captured by Fidelis
It's likely that, as happened to MongoDB victims, the attack volumes will rise in the near future. Within a week of those attacks, 'net scum had moved on to Elasticsearch. ®
