This article is more than 1 year old
Your body reveals your password by interfering with Wi-Fi
Wave goodbye to security if crims can pop a MIMO router
Modern Wi-Fi doesn't just give you fast browsing, it also imprints some of your finger movements – swipes, passwords and PINs – onto the radio signal.
A group of researchers from the Shanghai Jaio Tong University, the University of Massachusetts at Boston, and the University of South Florida have demonstrated that analysing the radio signal can reveal private information, using just one malicious Wi-Fi hotspot.
In this paper, published by the Association of Computing Machinery, they claim covert password snooping as high as 81.7 per cent, once their system has enough training samples.
It's an attack that wouldn't work if you had a primitive Wi-Fi setup with just one antenna, because it relies on the sophisticated beam-forming implemented in Multiple-Input, Multiple-Output (MIMO) antenna configurations.
In a modern Wi-Fi setup, beam-forming is controlled by software that uses the small phase differences between antennas to reinforce signals in some directions, and cancel them out in other directions.
That's what the researchers exploited: because the kit is designed to manage very small changes in signal, the researchers worked out the link state changes when the user's hand is moving near the phone – such as when they're using the screen input.
From their paper – its obligatory cute title is When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi Signals, where “CSI” stands for “channel state information: “WindTalker is motivated from the observation that keystrokes on mobile devices will lead to different hand coverage and the finger motions, which will introduce a unique interference to the multi-path signals and can be reflected by the channel state information (CSI)”.
The boffins are particularly pleased with themselves that they don't need to compromise the target: the attack is launched entirely from a malicious Wi-Fi hotspot.
A picture is probably useful at this point: this shows the CSI values recorded by the attackers if a user is continuously clicking different keys or the same key.
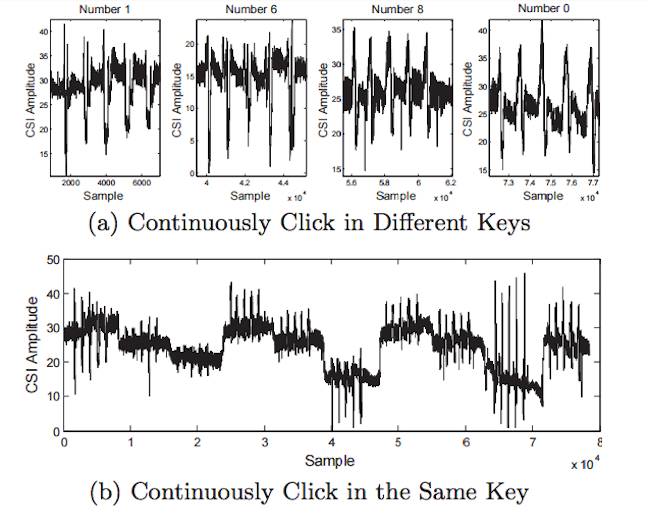
Channel state information (CSI) analysis reveals user's movements. Image from When CSI Meets Public WiFi
To force the target to send CSI to the base station, the attack sends an ICMP (Internet Control Message Protocol) request to the victim, which sends back an ICMP Reply. WindTalker only needs to gather 800 packets per second of replies to analyse the user's keystrokes.
As well as the signal analysis, the Wi-Fi base station was modified with a panel antenna for better sensitivity, and the researchers wrote WindTalker's software to watch out for HTTPS sessions (since that might alert them to when the user was hitting a payments site – AliPay was chosen for this experiment).
The researchers note that there's a simple way to block WindTalker: companies crafting payment apps should randomise their keypad layouts. The attacker can still infer the finger's position – but won't know what key was pressed. ®
