This article is more than 1 year old
Hilton hotels' email so much like phishing it fooled its own techies
Looks like a phish, swims like a phish, actually just a shiny marketing lure
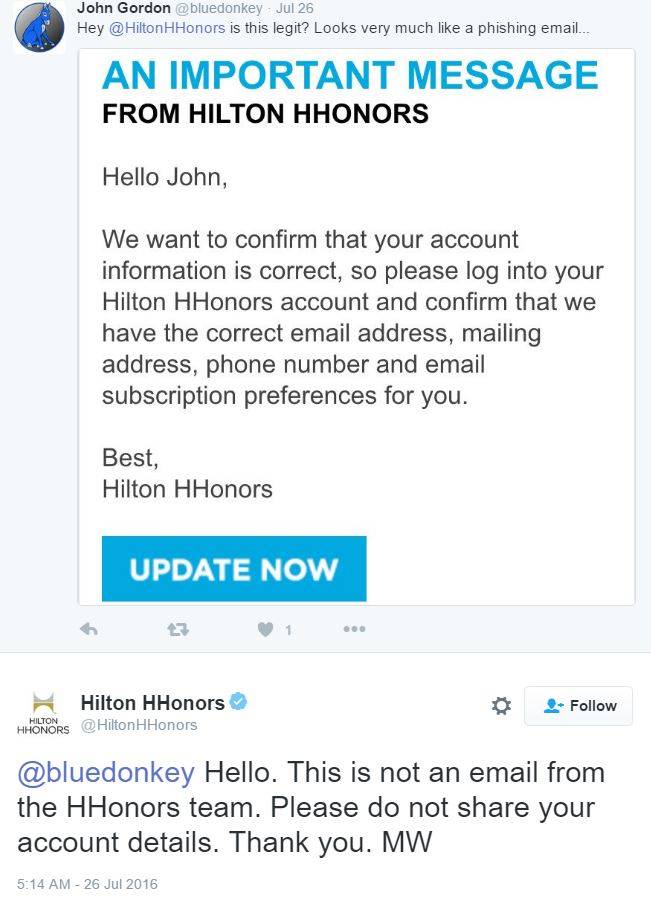
Hilton hotels' HHonors loyalty program has shipped an email so similar to a phishing email it tricked its own IT shop into advising that it was a scam.
The email was an attempt to get customers to confirm their contact details by logging into their accounts and revising their stored contact details.
One user reported the apparent scam to Hilton HHonors through Twitter and was advised that the email was a phoul phish.
It is one example of how legitimate email senders are creating opportunities for phishers, NCR Corp security man Lenny Zeltser, who published a proof copy of the HHonors email, says.
"... this email message looked so much like phishing that even Hilton’s own support team on Twitter thought it was fraudulent," Zeltser says
"The premise of the message is identical to that of numerous fraudulent emails that arrive in people’s inboxes.
"When customers learn to receive legitimate messages that look like this, they lose the the opportunity to distinguish between real and fraudulent messages."
Hilton is but one in a litany of organisations that craft emails containing the hallmarks of phishing. Such mails help to undermine the security advice users receive to help them avoid the world's most popular and effective attack vector.
Delta Airlines and others have done the same with flight points systems asking customers to change contact information via buttons within emails. Those include the target customer's identity number which Zeltser notes could be easily invented since few recall the combination from memory.
PayPal gets a tick for crafting the most polar phishing email with the inclusion of the customer's first and last name, a reference to a confirmed transaction and date, and use of the much-ignored DMARC protocol which allows email clients like Gmail to authenticate sending servers.
"From a security purist’s perspective", Zeltser says, customer emails should use top level links only from a homepage, should use DMARC, and use HTTPS for all embedded links to avoid data interception over hostile wifi networks.
It should also include specific customer information that an open source scourging phisher could not pluck from Facebook or Twitter, should ask customers to call phone numbers they need to look up on credit cards or websites,
"A more evolved approach would start with a minimalistic message that’s highly secure, then dial back some security attributes based on customer feedback," the security boffin advises organisations wedded to flashy buttons. "Be careful not to relax the characteristics too strongly; sometimes, non-technical users need to be protected even when they don’t realise it." ®