This article is more than 1 year old
Nasty session stealing hole filled in WordPress All in One SEO plugin
A million sites are at risk. Again. So patch, please
The developers have patched a hole in the popular All in One search engine optimisation WordPress plugin, a tool that's been downloaded by some 30 million users and is used on a million sites.
Flaws exist in the Bot Blocker component which can be exploited to steal administrator tokens and conduct actions through cross-site scripting vulnerabilities.
Users must upgrade to version 2.3.7 to guard against the flaw, which only manifests when users activate the tracked bot setting.
Dutch researcher David Vaartjes posted proof-of-concept code detailing how to exploit exposed sites.
He says attackers can lace request headers with malicious Javascript that will be logged inside the tracked bot panel page, and then executed to nab an admin's session token.
"A stored cross-site scripting vulnerability exists in the Bot Blocker functionality of the All in One SEO Pack WordPress plugin," Vaartjes says.
"Particularly interesting about this issue is that an anonymous user can simply store his XSS payload in the admin dashboard by just visiting the public site with a malformed user agent or referrer header.
"If the 'track blocked bots' setting is [deliberately] enabled, blocked requests are logged in that HTML page without proper sanitisation or output encoding, allowing XSS."
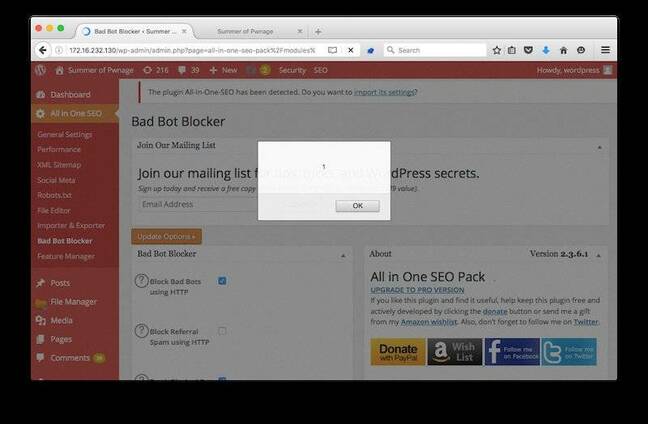
Proof-of-concept XSS demo
WordPress sites are a favourite for attackers, because scores of exploits target the core CMS and many more attack the many third-party plugins that enhance its functionality. Plenty of admins patch neither the CMS nor the plugins, or patch the CMS and neglect plugins that patch on different cycles. Whatever the reason for patches being missed, WordPress often ends up used often in command and control infrastructure to deliver exploit kits and various drive-by-downloads. ®
