This article is more than 1 year old
Hackers rely on weak passwords when brute-forcing PoS terminals
Open Sesame: '12345'
New research takes a fresh perspective on the passwords hackers use while scanning the web rather than the weak login credentials users often pick.
Security analysts Rapid7’s results come from a year’s worth of opportunistic credential-scanning data collected from Heisenberg, the MetaSploit firm’s public-facing network of honeypots.
Logs from these honeypots provides an insight into what opportunistic scanners are using in order to test – and likely compromise – internet-connected point-of-sale (PoS*) systems, kiosks, and compromised desktop PCs which offer the Remote Desktop Protocol (RDP) service for remote management.
The study, which focused on retail terminals, pulled out statistics on the frequency and source of opportunistic attacks, as well as the top attempted passwords and usernames. The overlap between these chosen credentials and published password dumps collected from breach data was also highlighted.
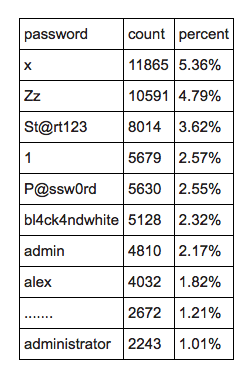
Instead of old favourites such as “12345” and “password” on the user side, credentials such as “x”, “St@rt123”, “P@ssw0rd” and “admin” appeared in the top 10 of password guessing attempts. Usernames of “administrator”, “admin” and “pos” were among the most frequently guessed in the hi-tech doorknob-rattling by hackers.
China was the most common source of login attempts (39.9 per cent) followed by the US (24.9 per cent) and, way back, by South Korea (6 per cent), in third pace. Russia didn’t even figure in the top 10, possibly because all the would-be PoS hackers in the country used proxies located elsewhere.
The findings show that the majority of passwords attempted are very simple, implying a belief by hackers in the widespread use of defaults and passwords chosen out of convenience instead of security necessity. Crooks who unwittingly took part in the study are essentially opportunistic thieves who continuously scan the internet for low-hanging fruit; specifically, systems with default login credentials which they can can subsequently hack.
A blog post by Rapid7 summarising the findings of the study can be found here.
Tod Beardsley, security research manager, Rapid7 said: "The research from Rapid7 takes a look at the state of credential security with a focus on point of sale (PoS) systems reachable from the internet, but instead on focusing on particular brands, models, or customers, it analyses the passwords used today by criminal attackers all over the world.”
“Research that combines active scanning and passive collection techniques is incredibly useful for spot checking the state of cyber hygiene, and we hope to continue this sort of research to help identify where enterprises and small businesses are faltering when it comes to their online footprint,” he added. ®
* Point of Sale, people, Point of Sale! (OK, even subs desk says Piece of Sh$t in our heads when we read it)
