This article is more than 1 year old
SAP pumps 70m barrels of oil a day ... and might also blow them up
Researchers find ways to p0wn industrial control systems
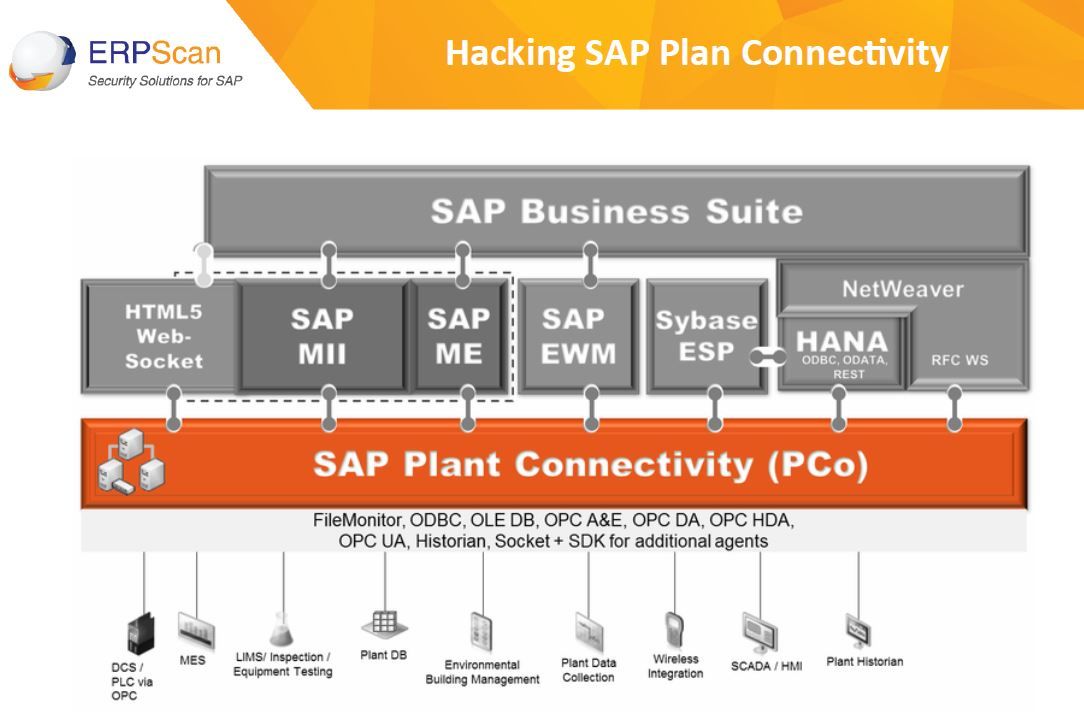
Blackhat Europe Security boffins Alex Polyakov and Mathieu Geli say SAP platforms can be used as bridges to cause physical damage by attacking industrial control systems.
The ERPScan duo say SAP often works with internet-facing industrial control systems. SAP companies represent 75 percent of the industry and produce 70 million barrels of oil a day.
Polyakov has previously found scores of vulnerabilities and notably misconfigurations in SAP deployments that expose sensitive user data.
And in May Onapsis chief executive Mariano Nunez says his company reckoned a whopping 95 percent of installations contained "high-severity" and ultimately hijackable errors in tests of 250,000 SAP customers.
Together it means the internet-facing SAP systems are at a higher risk of attack than what may be reasonably expected.
Polyakov and Geli presented the findings in a talk at BlackHat Europe titled SAP Cybersecurity for Oil and Gas which is their first look at the field.
In it they describe how attackers can gain access to upstream oil and gas miners, mid stream transport and processors, and downstream refineries and marketers.
Within the upstream the team say attackers could cause mayhem with burner management system by controlling the ratio of flammable mixtures.
The simplest attack here is to turn off purge functions but other attacks against ICS can lead to "multiple risks including explosion", or the shutdown of refineries, the pair say.
More boring hackers might be satisfied with popping SAP to toy with metering, altering the custody transfer between utilities such that a 0.1 percent error - a "tolerable" variance" - could fleece the victim of US$50 million in a year.
If industrial control system hacking is too audacious or complex, Polyakov and Geli recommend say hackers target the regular SAP business applications which will let them steal secrets, extort companies, or modify financial statements.
Would-be hackers should start their attacks on an industrial control system with reconnaissance pursuing press releases, Linkedin, and StackOverflow among other sources
The pair have published detailed slides (PDF here) on the affected platforms and steps of how an attacker could gain access to industrial control systems. ®