This article is more than 1 year old
Chinese popped-box VPN crims screamed hacker booty in cleartext
Terracotta found porous
China-based virtual private network provider Terracotta, a favourite of some of the most capable hacking groups, is pumping their stolen user credentials in cleartext.
The forehead-slapping gaffe was revealed by RSA fraud prober Kent Backman, while outlining more details about the Terracotta VPN organisation first described in August.
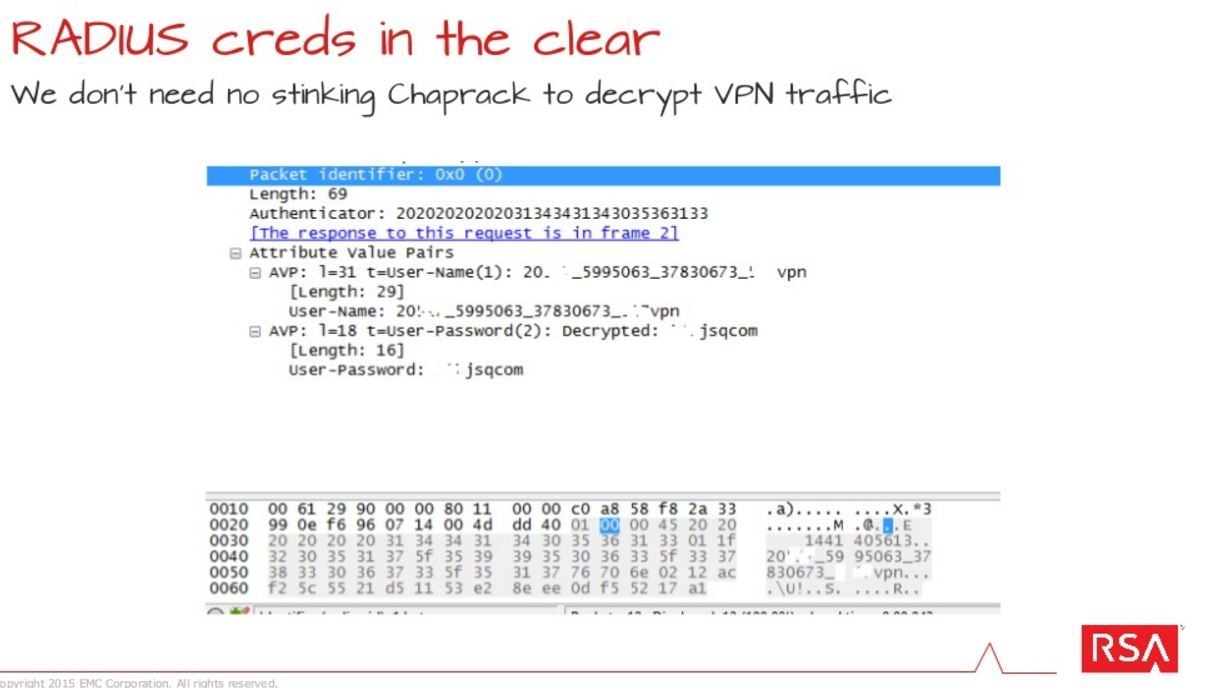
All of the nodes Terracotta uses to power its commercial VPN are popped boxes, Backman says, in what would help boost the unscrupulous seller's bottom line.
Most of the 1500-odd nodes are in China, with about 600 in the US.
Backman and fellow RSA bods Alex Cox, Steven Sipes, and Ahmed Sonbol revealed in the August paper Terracotta VPN: Enabler of Advanced Threat Anonymity [pdf] groups including Deep Panda use Terracotta, directly their criminal activity through hacked Fortune 500 companies and other businesses.
Other hacked organisations include a US transport agency, a US county government, and a high-tech manufacturer. All victims have compromised Windows servers and Routing and Remote Access installed.
The cleartext flaw means researchers or any other eavesdropper do not need to pop Terracotta's infrastructure to know what data its criminal customers are stealing.
"RSA Research has confirmed that Terracotta nodes send user account credentials to China in the clear," Backman said at the 44Con security meet last month.
By popping corporates Terracotta might be able to evade Beijing's block of VPNs which allows enterprises to tunnel but strikes down the OpenVPN protocol.
RSA tracked in one node over 30 days 118,948 successfully authenticated connections from 9053 unique IP addresses of which 98 percent originated in China. ®