This article is more than 1 year old
Slacker vendors' one-fix-a-year effort leaves 88% of Androids vulnerable
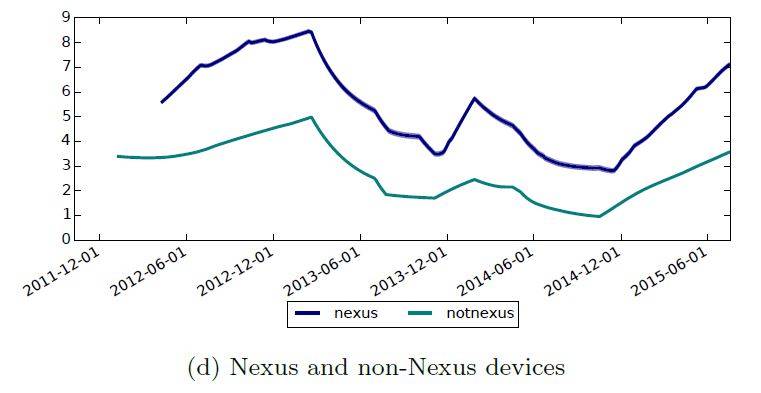
Nexus runs rings around rivals.
Android vendors are hopeless at distributing patches and users of new handsets can expect just one update a year, leaving most exposed to critical vulnerabilities according to a new study.
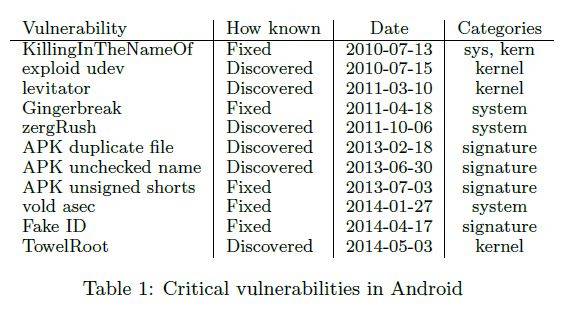
Cambridge University trio Daniel R Thomas, Alastair R Beresford, and Andrew Rice probed 20,400 devices and found 87.7 per cent contained at least one bad vulnerability that could leave handsets hosed.
They say in the Security Metrics for the Android Ecosystem (PDF) the 11 vulnerabilities allowed attacks like dynamic link loading and injection, and could let malware to hijack traffic, brick phones, replace apps, and steal user credentials.
The trio don't finger Google, users, and even telcos for the mess, instead finding the bottleneck lies with handset-makers.
The researchers, tasked with finding the most secure Android, say they have now created the beginnings of a framework that will help form a longitudinal study into how security varies between vendors.
Here's a little of their thinking:
The security of Android depends on the timely delivery of updates to x critical vulnerabilities. Unfortunately few devices receive prompt updates, with an overall average of 1.26 updates per year, leaving devices un-patched for long periods. We showed that the bottleneck for the delivery of updates in the Android ecosystem rests with the manufacturers, who fail to provide updates to x critical vulnerabilities. This arises in part because the market for Android security today is like the market for lemons: there is information asymmetry between the manufacturer, who knows whether the device is currently secure and will receive updates, and the consumer, who does not. Consequently there is little incentive for manufacturers to provide updates.
The group proposes a score to grade Android handset vendors based on their provision of patching in new devices and those updated after sale. It is intended as a metric by which users and regulators can act based on security risk.
From this score, Google's own Nexus is the clear winner, with LG earning a nod for fast patching. Those vendors have committed to monthly patches but not a start to that initiative.
Of the carriers, O2 UK is the best for pushing over-the-air security fixes just ahead of T-Mobile and Orange.
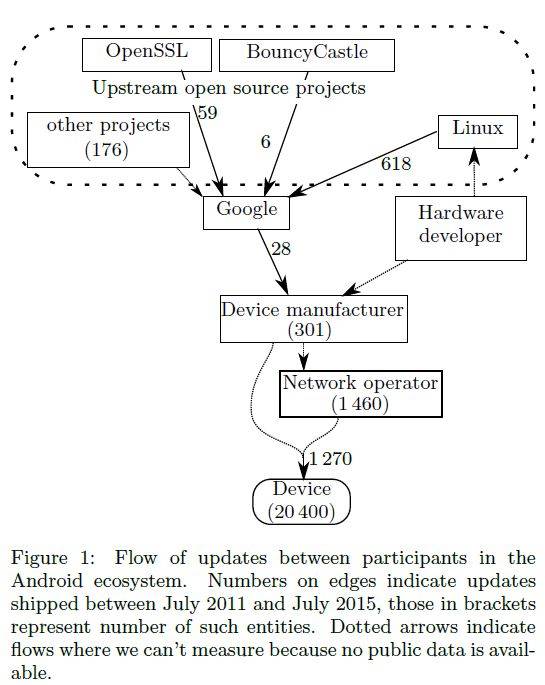
Participants in the patching architecture include network operators, device manufacturers, hardware developers, Google, and upstream open source projects.
Phones are determined insecure using the Device Analyser app which offered information on the build string and `x.y.z opaque marker' which reveals what patches are applied. ®