This article is more than 1 year old
Sony Pictures in IT lock-down after alleged hacker hosing
Data caches uploaded as hackers deface internal staff boxes
Sony Pictures is investigating a breach that has seen hackers supposedly steal reams of internal data and splash defacements across staff computers. The company is now in lock-down as it wrestles with the problem.
The beleaguered company, writes Variety, has requested staff disconnect their computers and personal devices from the Sony network and shut down virtual private networks.
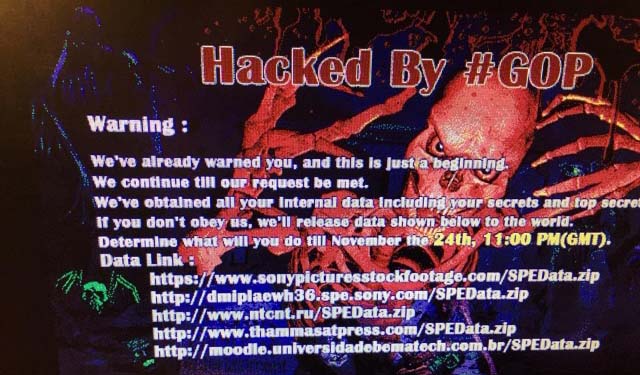
Cracking group Guardians of Peace claimed responsibility for a defacement appearing on staff machines that it stole internal corporate data. The group says it will leak more details to the public web depending on what Sony 'decided' in what appeared to be a reference to demands quietly sent to the company earlier.
Users have overloaded servers hosting the alleged 200Mb-plus breach caches grinding many to a crawl.
The group also hacked dozens of Twitter accounts linked to movies such as Stomp The Yard, Soul Surfer, and Starship Troopers.
News broke after a user claiming to be a former Sony staffer posted allegations of the breach, including the defacement picture on Reddit. The account was a year ago linked to posts claiming to be a Sony employee and has since been deleted.
Sony spokeswoman Jean Guerin said it was "investigating an IT matter" but could not confirm the hack.
"Hacked By #GOP Warning: We've already warned you, and this is just a beginning. We continue till our request be met. We've obtained all your internal data, including your secrets and top secrets. If you don't obey us, we'll release data shown below to the world. Determine what will you do till November the 24th, 11:00 PM (GMT).
Users have searched the alleged Sony data caches dumped online and reportedly found private PuTTY SSH keys, passwords for Oracle and SQL databases, source code and production schedules and hardware inventory lists.
Included files were named 'Jana's passwords.xls', 'Extranet Oracle & SQL passwords 4.3.06.txt', and 'ACCOUNTS WITHOUT PASSWORDS.xls'.
At least 20 SSH keys were allegedly discovered by inquisitive users downloading the released data with one named AkamaiPrivateKey.ppk.
An alleged group of document file names was published online a user who downloaded some of the data caches.
The Reg will update this story as more details become available and once the trove downloads. ®