This article is more than 1 year old
Data retention: encryption won't protect you much
Australia's mass data retention plan remains a bad idea, with or without crypto
The standard infosec advice of “encrypt it all and use strong passwords” is good advice, but it wouldn't save us from governments intent on mass data collection.
In this piece in The Guardian, Paul Farrell notes that metadata collection is a threat to journalism.
His point is quite simple: Australia already allows metadata access under rules that are so loose that if, for example, a journalist received information from a Treasury whistleblower, that department could issue a metadata request.
If a telecommunications carrier complied with that request, it would collect the metadata of a journalists' future communications, and hand that over for investigation to see if the whistleblower and journalist had contact.
That might not yield anything, since the journalist and whistleblower could be prudent enough to stay away from each other after the leak. However, if a data retention regime were implemented, the story changes: if the whistleblower used any identity or phone number known to the department, the contact between the two would be discoverable in the journalist's metadata.
Farrell then notes:
“If there hasn’t been a level of obfuscation or encryption used by the journalist and the source, it's a relatively simple task to track down the source using this information.”
Metadata is, as I said, misunderstood – and that's hampering the debate. While obfuscation – for example, contacting a journalist from an account that doesn't reveal your identity – is a good thing, encryption doesn't protect identities.
Here is a simplified representation of an IPv4 packet:
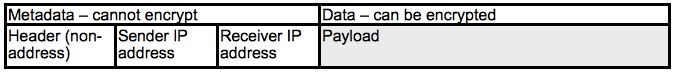
The greyed-out section – the payload – is the part that's encrypted, which is as it must be. You can't encrypt addresses, because all of the routers between you and the other end of a communication have to know where they're sending the packet (please don't tell me I've left stuff out – I mention the layering later).
That packet is, of course, generic: it might be your Web browsing, your e-mail, a VPN connection to Netflix or anything else. The only way to tell, from packets alone, that this packet might contain e-mail is if you're communicating with an IP address associated with an e-mail server.
It's easy to think that this should be enough to protect the user. The sender and recipient of an e-mail are carried as part of the packet payload – if you're using a secured login or if the provider requires it, then even the e-mail metadata (sender, recipient and subject) are travelling as part of the IP payload.
Right? Not quite
Right, but only as far as the server, where the payload is decrypted. If the provider were subject to a retention regime, then that metadata will be in its system logs, and encryption doesn't protect you at all.
The e-mail example also neatly illustrates what ISOC-AU's Narelle Clark told the Senate Committee looking into the Telecommunications Interception Act: the lack of definition around what is “metadata”.
The Attorney-General's Department – it would be unfair to single out a single A-G in this discussion – schools its incoming political masters, whomever they may be, that “metadata” is simply “non-content” data.
They're drawing their analogy from telephony, where the division is clear and standardised. In the world of the Internet, what's “content” data and what's “metadata” depends where you look. On the wire, an Ethernet frame consists of “metadata” – for example, source and destination MAC addresses – and “data”, which is whatever is put in the frame. At that layer, everything important would be protected.
So it goes, each layer up – the line between metadata and data only applies within the layer you're looking at. The IP packet has a header (its metadata) and a data frame; the TCP packet, likewise, has metadata and data; the application (for example e-mail), ditto.
To distinguish these would, I suspect, be objectionable to law enforcement. The steady mission creep of law enforcement is drifting towards “whatever we can justify keeping”: a fuzzy definition is preferable.
Spooks push back
It seems no coincidence to Vulture South that during the Senate Committee hearings, the spooks have decided to start no-names briefings and story drops to drive home their message that The Internet is A Scary Place.
Hence “sources say” that the alleged Chinese hack of the Australian parliamentary computer network, later explained as an attempt to get the plans for the Australian Security Intelligence Organisation's new headquarters, was worse than we thought.
The Australian Financial Review looks like it has received an insider briefing that the hackers had open access to the Parliamentary network for as much as a year, even though the same story suggests that the Defence Signals Directorate (now the Australian Signals Directorate) knew what was going on:
“The intelligence services briefed the parliamentary committee that oversees security matters while it was in progress, sources said, and the network was shut down several times while analysts from the Australian Signals Directorate patched it. 'It was like an open-cut mine,' said one participant. 'They had access to everything.'” and “senior sources say the Australian Signals Directorate, then called the Defence Signal Directorate, was aware of the breach and had assigned a 'tiger team' of 10 experts to fight off the Chinese intruders and rebuild the network’s defences”.
“Encrypt everything you can encrypt” is still good advice, even in a world that knows about Heartbleed. Just don't mistake encryption for protection – and don't give spies and police unfettered access to system logs. ®
