This article is more than 1 year old
Google personal suggest bug exposed user web history
Data hole plugged after impersonated keystroke attack
Google has restored its "personalized" search suggestions after purging the tool of a critical vulnerability that allowed attackers to steal a user's web history.
Personalized search suggestions were disabled on March 1, and they didn't return until April 20. Ordinarily, Google adds these personalized keyword suggestions to its generic suggestion list if you've turned on Google Web History, a service that stores your searches and page visits. The personalized suggestions are based on data from Web History.
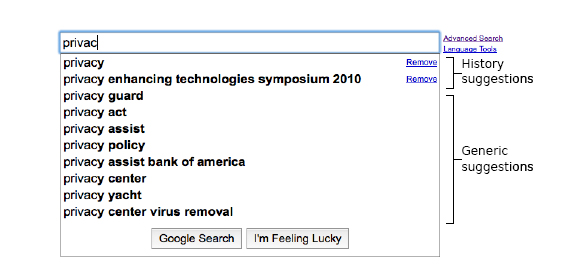
Google's personalized search suggestions tap Web History data
In late February, a trio of security researchers - one at the University of California, Irvine and two at the French National Institute for Research in Computer Science and Control (INRIA) - sent Google a preliminary version of a paper showing how they were able to infer large portions of a user's web history by hijacking the user's session ID (SID) cookie and nabbing the company's personalized suggestion data. Google quietly disabled the personalized suggestions a week later.
Then, on March 15, the company sent a statement to the researchers saying it had added SSL decryption to Google Web History and that it had started encrypting the back-end Web History server requests used to personalize suggestions on its Maps site. Google also said it would "soon" do the same for search, and this happened more than a month later.
Google tells The Register that personalized search suggestions took longer to restore because the fix was "more complex to deploy and involved a larger code change."
The company also points out that it has been much quicker to add SSL encryption to its online services than competitors - which is true. In July 2008, the company added an HTTPS-only option to Gmail, and in mid-January, hours after announcing that alleged Chinese had pilfered intellectual property from its internal systems, it turned the encryption on by default. It also offers SSL as an option on its Calendar, Docs, and Sites services.
Yahoo Mail and Microsoft Live mail still have not offered such protection.
“We highly value our relationship with the security research community, and we are grateful to Dr. Castelluccia and his fellow researchers from INRIA and University of California, Irvine who have been in contact with us since the end of February about their findings related to open, unsecured network connections and personalized suggestion technology." reads the statement, which was later sent to The Reg after it was changed to reflect that personalized search suggestions have now been restored.
"Google has been and continues to be an industry leader in providing support for SSL encryption in our services, which is designed to address precisely the issues that all major websites face when transmitting information over http to users connecting via an unsecured network channel." When adding SSL to Google Web History, it also began encrypting its Bookmarks online service.
Emiliano De Cristofaro, the University of California Irvine researcher who contributed to the paper sent to Google, tells The Reg the reported attack was designed to show "the dangers of the concentration of personal information at large service providers." And Google was the obvious place to start. "If providers do not provide fully secure services - as was the case with Google Web History - sooner or later you will be able to find a leak," he says. "These kinds of information should always be encrypted."
With their attack - which they call the Historiographer - the researchers were able to pilfer a user's session ID (SID) cookie on an unsecured wireless network and then grab Google's personalized suggestion data by - in essence - pretending to be the user. Google sends new suggestions with each user keystroke, and it only sends personalized suggestions if what the user has typed corresponds to sites that according to Web History, the user has searched for in the past and actually clicked on. By "impersonating" several hundred user keystrokes, De Cristofaro says, the researchers were able to reconstruct "a very large part" of all "clicked searches" stored by Web History.
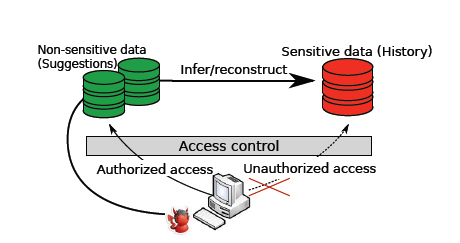
Researcher's illustrate attack on Google Web History
Each personalized suggestion is tagged with a "Remove" link, which lets you, yes, remove that particular search from Web History. The researchers could easily recognize the Javascript containing each personalized suggestion, and each suggestion corresponded to a clicked search in the user's Web History.
Details of the researchers' reconstruction algorithm are available here. "Within a few seconds of eavesdropping, [the attack] can reconstruct a significant portion of a user’s search history," the paper reads. "This may have been populated over several months and from many different locations, including those from where a privacy-conscious user avoids sensitive queries fearing traffic monitoring."
But Google's changes mean the attack no longer works. The researchers are now looking for a similar hole in Microsoft's Bing suggestions, which launched on March 1. Unlike Google, Bing associates the user's web history with an anonymous cookie stored on the user's local machine for no more than 29 days. ®
