This article is more than 1 year old
Happy VXers get 400 enterprise-popping apps hosted on Google Play
Up to half a million downloads clocked for one poision app.
More than 400 malicious apps from a single attacker have been successfully uploaded to the Google Play store, with one downloaded up to half a million times, Trend Micro malware researcher Echo Duan says.
The malware is disguised as various games, phone boosters, and themes that when executed can compromise devices and connected networks, download additional payloads, and enslave handsets into botnets.
Such malware is usually barred from the Google Play store thanks to security analysis checks Mountain View runs to determine apps that steal user data, spam with advertisements, or adversely impact privacy.
The prolific authors who have created some 3000 variants of the DressCode malware have had a significant win in breaching Google's defences since apps hosted on the Play store are considered and marketed as safe.
Duan says the malware attempts to gain a foothold on any networks the compromised handsets are connected to making it a threat to to enterprises and small businesses.
This malware gives attackers an avenue into internal networks which compromised devices are connected to—a notable risk if the device is used to connect to company networks.
"If an infected device connects to an enterprise network, the attacker can either bypass the NAT device to attack the internal server or download sensitive data using the infected device as a springboard," Duan says.
"With the growth of bring your own device programs, more enterprises are exposing themselves to risk via care-free employee mobile usage.
"[The installed SOCKS proxy] can be used to turn devices into bots and build a botnet."
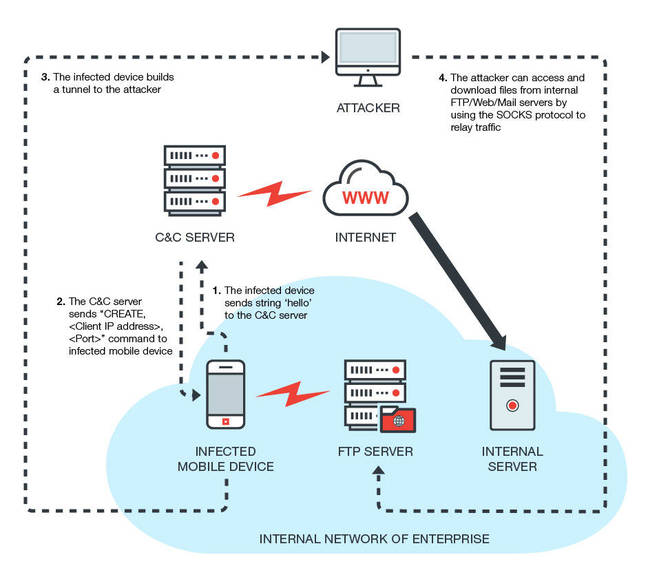
DressCode and you. Image: Trend Micro.
Duan says the malicious code was a small fraction of the total app codebase making it "difficult" for Google to detect.
One app offering a Grand Theft Auto theme for Minecraft clocked between 100,000 and 500,000 downloads according to Google Play's metric bands.
Compromising modern Android handsets is increasingly difficult for regular malware players thanks to big leaps in defensive upgrades, but most phone users run old, unsupported, and dangerously exposed versions of the mobile operating system.
Some 35 percent of Android users operate version five (Lollipop) of Google's platform released in 2014, while about 25 percent run ancient version 4.4 (Kitkat) published in 2013.
Fewer than 10 percent run Android version six (Marshmallow) released last year and virtually no one other than owners of Nexus 6P devices sports version seven (Nougat) published last month.
Outside of the Nexus line, handsets everywhere are locked into custom vendor ROMs and as such must reply on manufacturers to push through Google's security updates and patches.
Trend Micro says it flagged some 16.6 million malware detections as of August, 40 per cent up on January figures. ®
