This article is more than 1 year old
Medical data, staff creds exposed as scores of apps bork the backend
HAVOC tool rips out keys stored inside apps.
Blackhat Europe And still we fail to learn: a quintet of researchers has found that the bad practice of writing keys into code persists among some of the world's most popular Android and iOS applications.
The researchers say the hard-coded credentials can be easily extracted to gain access and manipulate millions of sensitive individual and corporate credentials, medical health records, and personal data.
The flaws exist in how thousands of apps connect to commercial backend services and expose sensitive user records.
They found 1,000 credentials from two million apps tested, providing access to a staggering 18.7 million records and 56 million data items. Backend services reduce the knowledge developers need to have to build apps by providing basic services and cloud storage.
The team also published the HAVOC tool that can automatically discover vulnerable apps and rip out keys for testing against relevant backend services.
Siegfried Rasthofer; Steven Arzt; Robert Hahn; Max Kolhagen, and Eric Bodden of the Technical University and Darmstadt, Germany, presented their work in the paper (In)Security of Backend-as-a-Service (PDF) presented at BlackHat Europe.
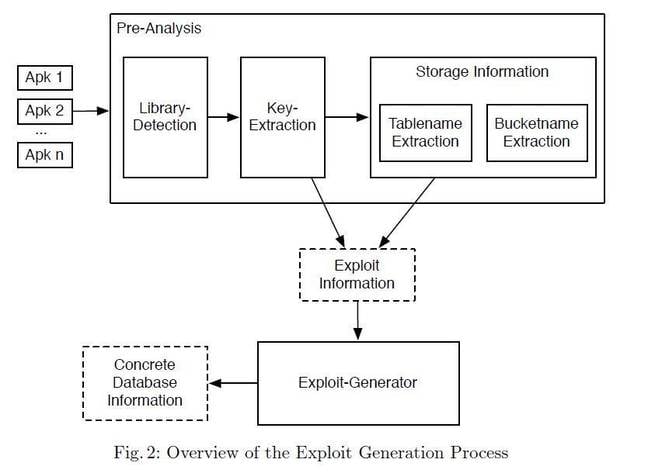
The authors describe their work as the first "comprehensive security evaluation" of BaaS providers and APIs, and its use in Android and iOS.
"We show that with current tools attackers can gain access to huge amounts of sensitive data such as millions of verified email addresses, thousands of health records, complete employee and customer databases, [and] voice records," they write.
"Often, one can manipulate, and delete records at will. Some BaaS instances even suffer from remote code-execution vulnerabilities.
"We provide HAVOC, a fully-automated tool for finding potentially vulnerable applications and a fully-automated exploit generator that extracts the required credentials from the app and checks their validity with the BaaS backend."
The team suggests developers and providers use more security-focused default credentials, educate developers on the threats, and for and automatic vulnerability scanning for applications uploaded to app stores.
"In general, app developers need to better understand that every app has security implications, which must be taken into consideration as part of the basic design of the app," they say. ®
