This article is more than 1 year old
Killer ChAraCter HOSES almost all versions of Reader, Windows
Google Project Zero bod drops 15 remote code execution holes
Get patching: Google Project Zero hacker Mateusz Jurczyk has dropped 15 remote code execution vulnerabilities, including a single devastating hack against Adobe Reader and Windows he reckons beats all exploit defences.
The accomplished offensive security researcher (@j00ru) presented findings at the Recon security conference this month under the title One font vulnerability to rule them all: A story of cross-software ownage, shared codebases and advanced exploitation [PDF ] without much fanfare and published a video demonstration of the exploit overnight.
The nastiest vulnerabilities for 32-bit (CVE-2015-3052) and 64-bit (CVE-2015-0093) systems exist in the Adobe Type Manager Font Driver (ATMFD.dll) module which has supported Type 1 and Type 2 fonts in the Windows kernel since Windows NT 4.0
Jurczyk says his 'entirely reliable' BLEND instruction exploits relate to the handling of CharStrings that are responsible for drawing the shape of each glyph at a particular point size.
"The exploit defeats all modern user and kernel-mode exploit mitigations, with the only non-fully deterministic step being kernel pool spraying [that is] working with 100 percent reliability in the tested environments," Jurczyk says.
"The video demonstrates reliable exploitation of a vulnerability in the handling of the BLEND instruction in Type 1 fonts, used in two stages to first achieve arbitrary code execution in Adobe Reader 11.0.10, and further escape the sandbox and elevate privileges to System by attacking the Adobe Type Manager Font Driver in the Windows 8.1 Update 1 32-bit (or 64-bit) kernel."
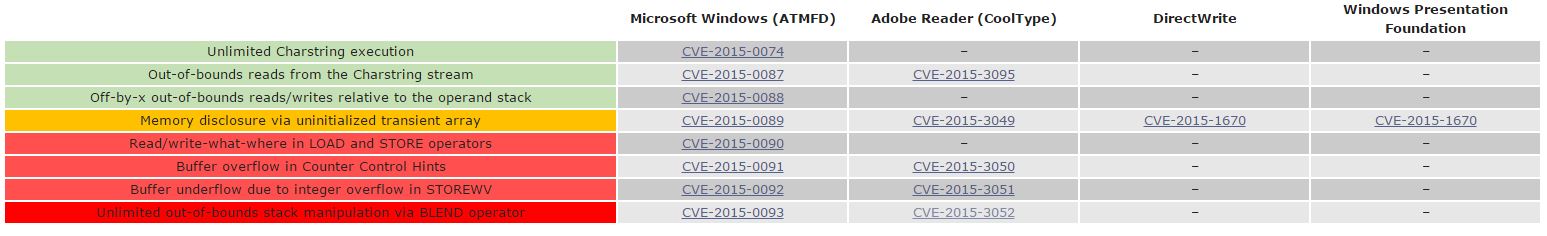
A summary of Jurczyk's carnage. Click here to embiggen.
Microsoft and Adobe issued patches in three updates.
Any of the 15 vulnerabilities Jurczyk pulled from this old but seemingly unexplored area could trigger remote code execution or privilege escalation in Adobe Reader or the Windows kernel.
@j00ru did you just.nonchalantly drop 15 CVEs in a single blogpost..?
— Sergiusz Bazański (@q3k) June 24, 2015
The BLEND exploit stands out as one of the hacker's most interesting finds in his career, in that it allowed attackers to generate a return-oriented programming chain leading to total system compromise against all versions of Adobe Reader and Windows.
"The extremely powerful primitive provided by the vulnerability - together with the fact that it affected all supported versions of both Adobe Reader and Microsoft Windows thus making it possible to create an exploit chain leading to a full system compromise with just a single bug – makes it one of the most interesting security issues I have discovered so far," he says .
The hack is made successful on 64-bit builds thanks to the addition of a separate CharString vulnerability (CVE-2015-0090) Jurczyk found from his research. ®
